When I saw https://cacheflowe.com/art/digital/deepflat I was “nerd sniped”. I had to figure out how to do it. A bunch of coffees later…
What’s better? I have source code!
When I saw https://cacheflowe.com/art/digital/deepflat I was “nerd sniped”. I had to figure out how to do it. A bunch of coffees later…
What’s better? I have source code!
Over the past few months our team at Clemson worked with TigerOne, our card services department, and Apple to successfully bring mobile ID provisioning to campus. We were the first school to integrate this functionality into our own app, my.Clemson, and that integration correlated with the success we saw on launch day – around 4500 students, faculty, and staff were able to add their TigerOne Mobile ID to their phone and Watch. These are record numbers to date. 🎉
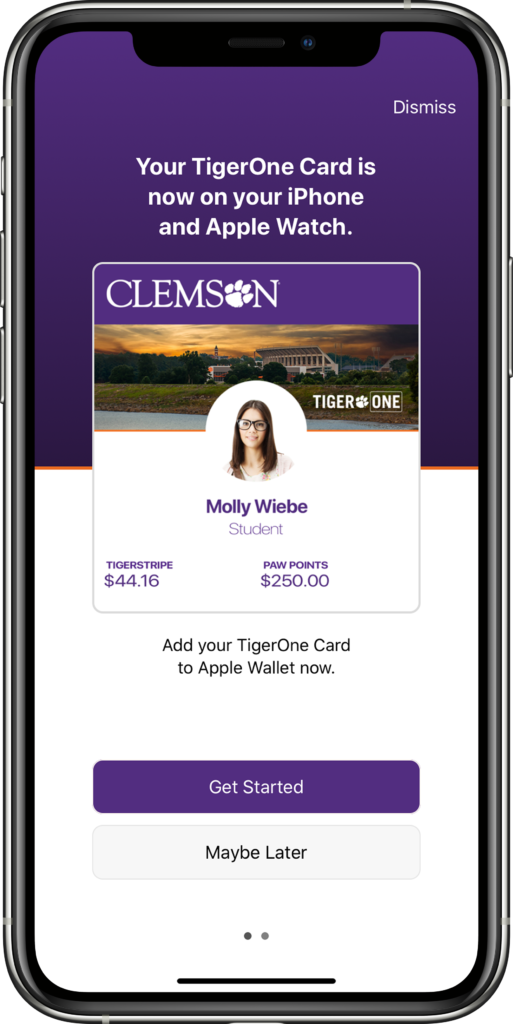
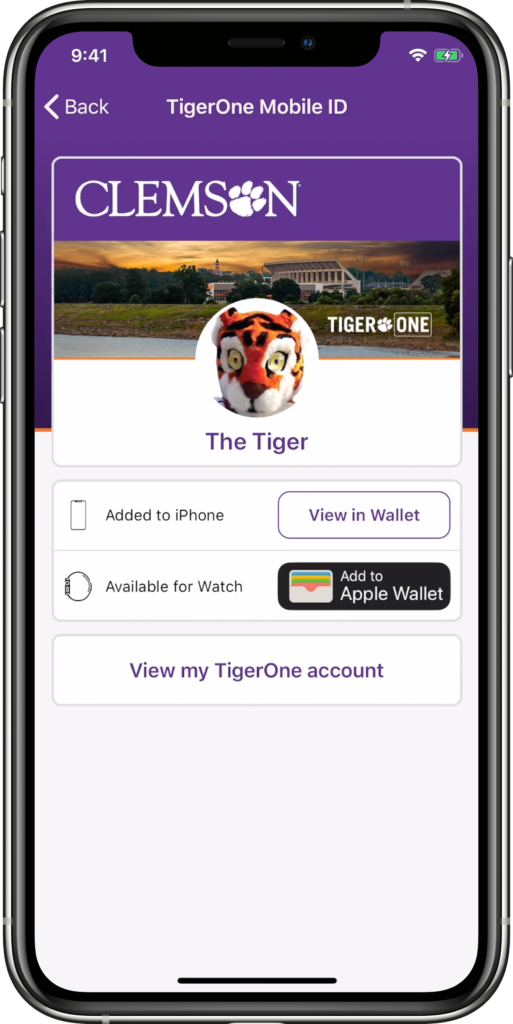
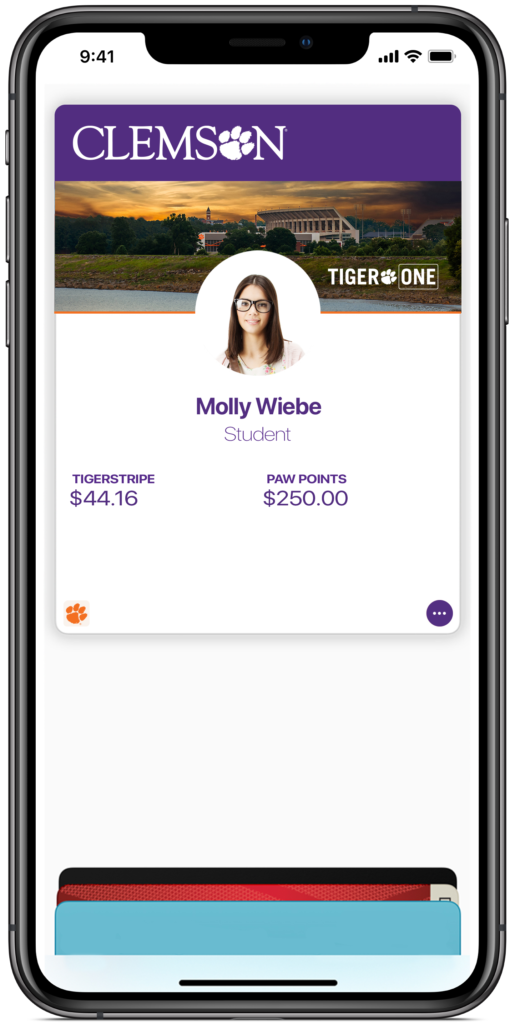
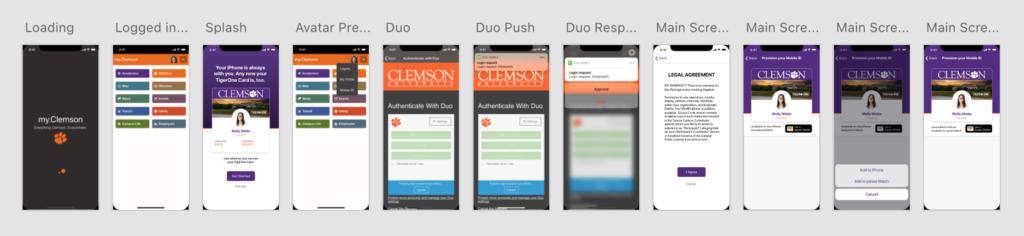
There were a lot of unknowns when we started the project, one being that we’d never integrated Duo (the University’s two factor system) with a native client. It made sense to reuse the embedded web version so we didn’t have to reinvent the wheel, but we weren’t sure of how to combine this with our current method of authentication via SwiftECP, whose goal is to avoid the browser!
We ended up with a pretty slick solution. After configuring the IdP to allow a Duo flow from a client that authenticated ECP, it worked like this:
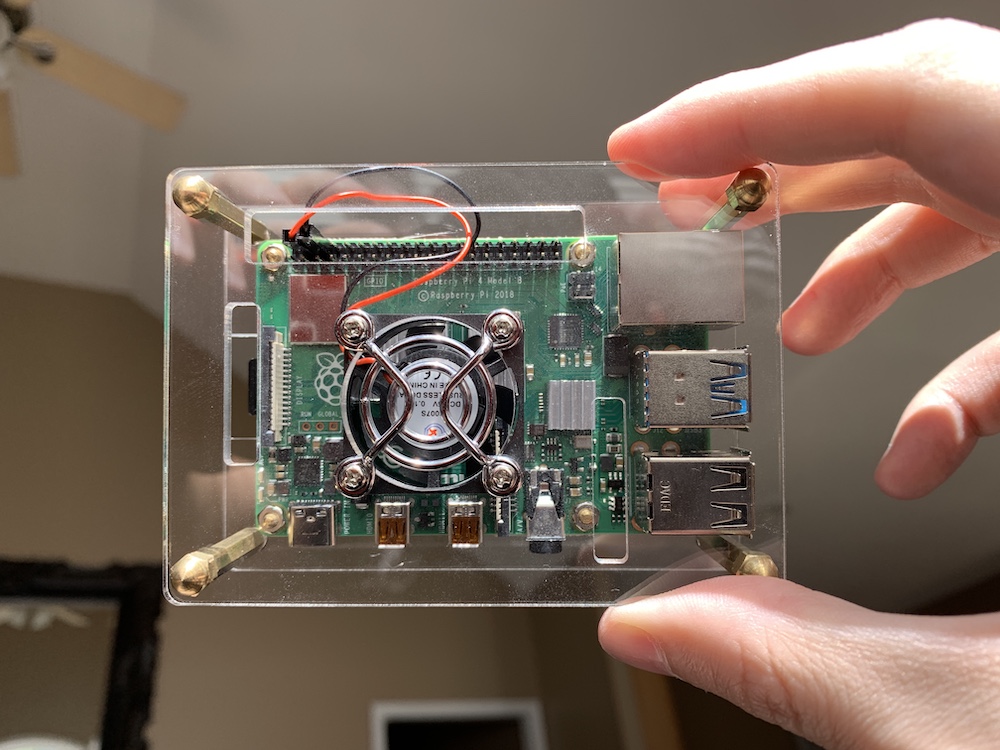
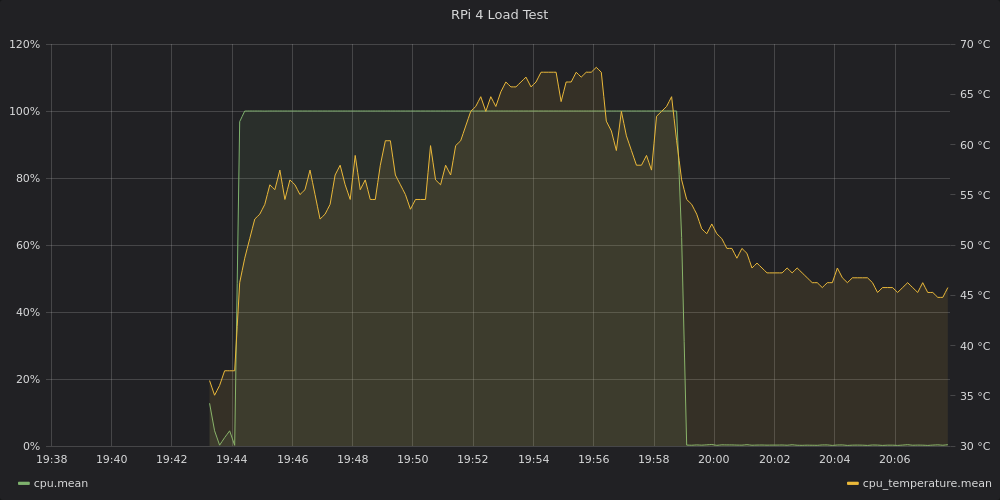
My excitement for the new Raspberry Pi 4 turned into disappointment upon learning it couldn’t handle sustained loads without some sort of extra cooling solution. After installing it in this case, I’m happy to say things are looking stable.
The Rover got its own iOS app and I implemented a neat way to control the camera servos.



This was a fun challenge (and a total hack). In the end it wasn’t that sophisticated, but it was a good exercise in UDP as well as data compression.